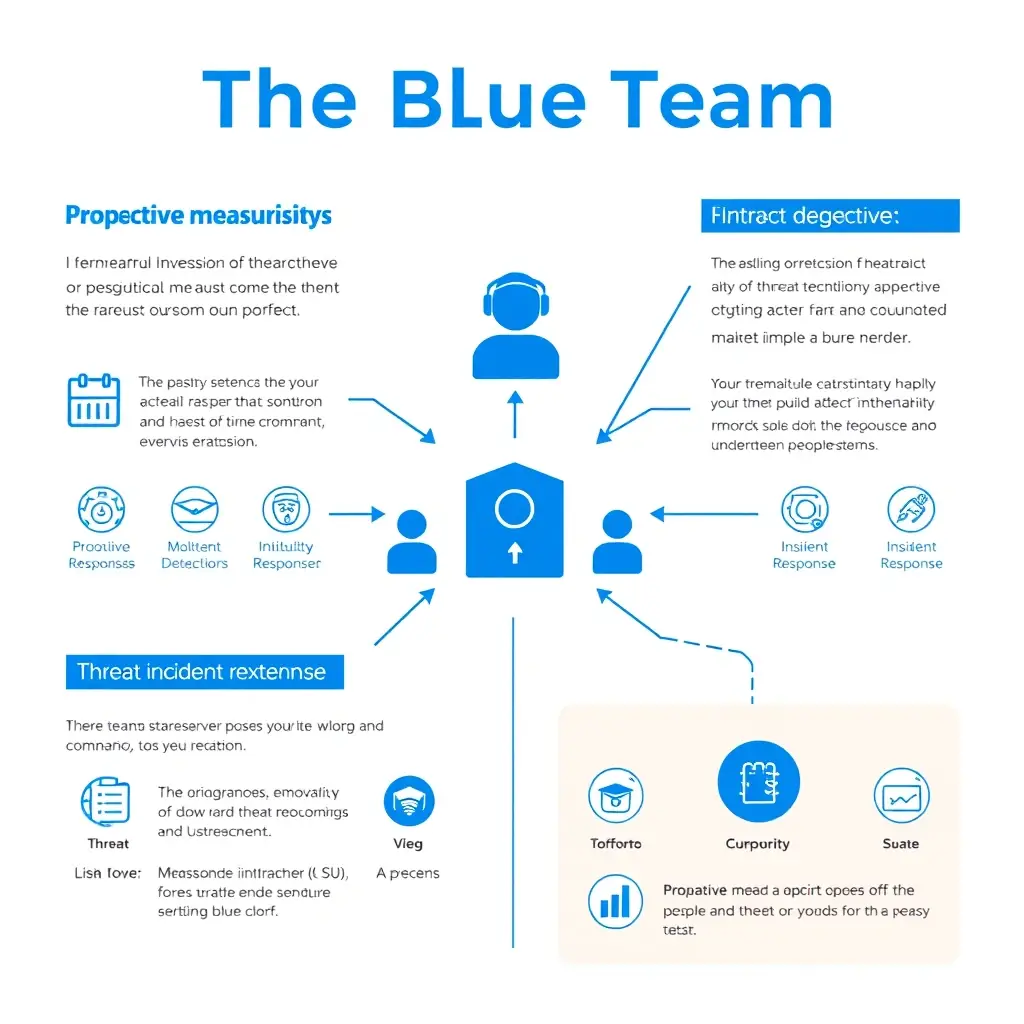
Understanding the Blue Team Role
The Blue Team plays a vital role in cybersecurity, focusing on proactive defense and threat detection. They are responsible for monitoring systems, analyzing logs, and responding to incidents to safeguard digital assets effectively.
0
%
This team ensures that organizations can detect and respond to threats before they escalate, maintaining a secure environment.
0
incidents
Their work involves continuous improvement of security measures and strategies to counteract evolving cyber threats.
0
alerts
By utilizing advanced tools and techniques, the Blue Team enhances the overall security posture of an organization.
0
vulnerabilities
They also conduct regular training and simulations to prepare for potential attacks, ensuring readiness at all times.
Mastering SIEM and Log Analysis for Robust Cybersecurity Defense
Explore the critical role of SIEM in cybersecurity. Learn how it works, its key features, and how it aids in threat detection and response. Discover common SIEM solutions and best practices for effective log management in a SOC environment, essential for ethical hackers and Blue Team members.
- SIEM Fundamentals: Understand the core principles and architecture of SIEM systems.
- Log Analysis Techniques: Learn to analyze various log types for threat hunting.
- SIEM Solutions: Explore popular SIEM tools like Wazuh, ELK Stack, and Splunk.

Strengthening Your Security Posture with Proactive Defense
Proactive defense is crucial for staying ahead of cyber threats. Unlike reactive approaches, it anticipates and neutralizes threats before they impact your systems. By implementing proactive strategies, you significantly enhance your organization’s security.
- Threat Hunting: Actively search for hidden threats within your network.
- Endpoint Hardening: Secure individual devices to minimize vulnerabilities.
- Patch Management: Keep systems updated to prevent exploitation of known flaws.

Mastering Attack Detection: A Blue Team's Guide
Learn how Blue Teams detect and mitigate cyber threats using behavioral analysis, anomaly detection, and pattern matching. Explore various attack types and detection tools to enhance your cybersecurity skills.
- Behavioral Analysis: Identify malicious activities by monitoring user and system behaviors.
- Anomaly Detection: Detect deviations from normal patterns that may indicate an attack.
- Pattern Matching: Use known attack signatures to quickly identify and respond to threats.

Enhance Your Blue Team Capabilities with Key Security Tools
Explore the synergy of Wazuh, ELK Stack, Zeek, and Suricata in enhancing your cybersecurity infrastructure. These tools provide comprehensive visibility, advanced threat detection, and robust log analysis, essential for effective Blue Team operations. Learn how to integrate and leverage these technologies to proactively defend against cyber threats and maintain a resilient security posture.
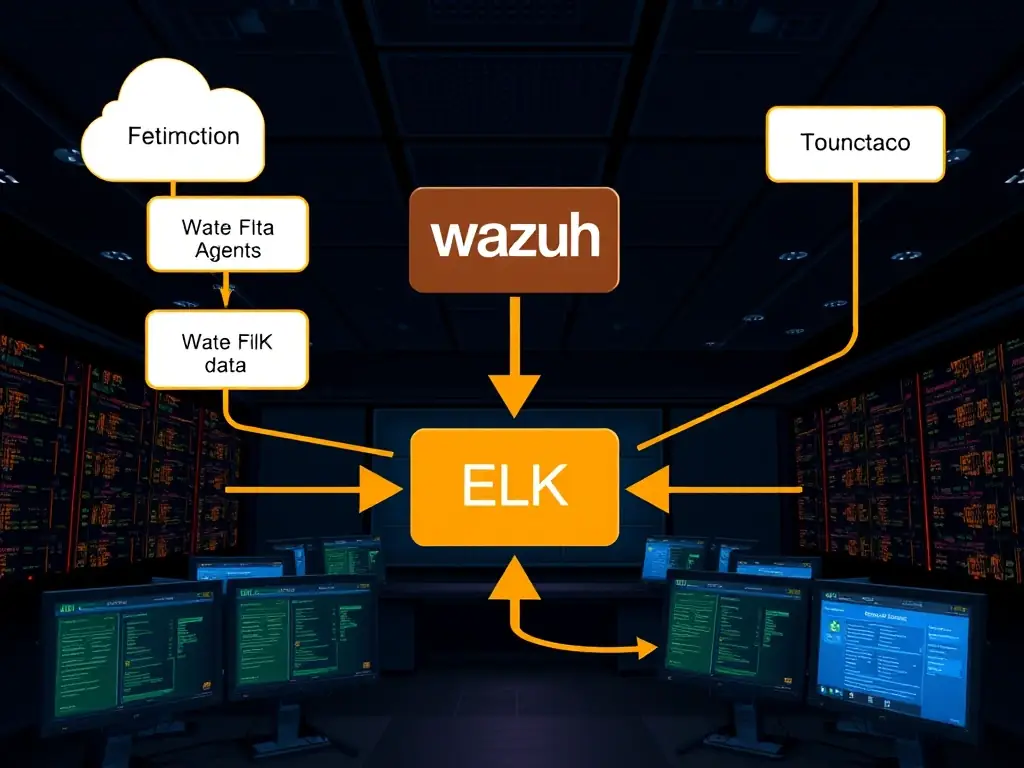
Wazuh and ELK Stack Integration
Wazuh, combined with the ELK Stack, offers a scalable solution for security monitoring and threat detection. It provides real-time insights into your infrastructure's security posture, enabling proactive threat management and incident response.
Zeek for Network Traffic Analysis
Zeek excels at deep packet inspection and network behavior analysis, providing invaluable context for security investigations. Its scripting language allows for custom rule creation, enhancing its ability to detect sophisticated attacks.

Suricata Intrusion Detection System
Suricata is a powerful intrusion detection and prevention system that uses rule-based detection to identify malicious activity. Its open-source nature and active community make it a cost-effective and adaptable solution for Blue Teams.

Unlocking Threat Detection with Sigma and YARA Rules
Sigma and YARA rules are essential tools for threat detection, enabling analysts to identify malicious activities and artifacts. Understanding their structure, syntax, and application is crucial for effective cybersecurity defense. At CyberLab, we provide the resources to master these skills.
- Sigma Rules: Learn to write generic signatures for SIEM systems.
- YARA Rules: Master pattern-matching for malware identification.
- Custom Rules: Create tailored rules for specific threat landscapes.
Enhance Your Skills with CyberLab's Blue Team Resources
At CyberLab, we provide a wealth of resources to help you master Blue Team techniques. Our platform includes practical labs for hands-on experience, detailed guides for certification preparation, and a comprehensive collection of technical books to deepen your understanding of cybersecurity defense strategies.

Practical Labs for Hands-On Experience
Our practical labs offer real-world scenarios to hone your incident response and threat detection skills. Dive into simulated environments and apply your knowledge to defend against cyberattacks.
Detailed Certification Guides
Prepare for industry-recognized certifications with our detailed guides. We provide step-by-step instructions, practice exams, and expert tips to help you succeed in your certification journey.

Comprehensive Technical Books
Access a vast library of technical books covering essential Blue Team topics. Expand your knowledge with in-depth analysis, case studies, and expert insights from leading cybersecurity professionals.
